In this article, I will walk through configuring and setting up all the Azure services needed to secure your account. There are many services available, but it can be difficult to understand what needs to be done to actually get protected and ensure that all assets are covered.
This is a broad topic, with a lot of nuance, so I will focus on the exact Azure services needed for a security program, and how to get started using them. Azure was built with security in mind, so compared to my articles on configuring AWS security, this is much more straightforward. I have found that Azure generally makes it easier to achieve strong security.
Setting up a solid cloud security program generally consists of a few key components:
- Centralize logs from all cloud resources, and make sure they are stored in perpetuity (for investigations as needed, ideally in low cost long term storage)
- Monitor the logs for suspicious events, and alert into your SIEM
- Configure automated configuration enforcement for the environment, so that teams can't make security mistakes (like deploying a database to listen for connections from anywhere)
To Achieve all of the above, we'll be leveraging the following services:
- Log Analytics to gather logs from our services
- Security Center for best practices (assets and subscriptions)
- Defender for automated threat analysis and indicators of compromise.
- Azure Sentinel for our SIEM (but you can integrate it with your existing SIEM as well)
- Azure Policy for security governance.
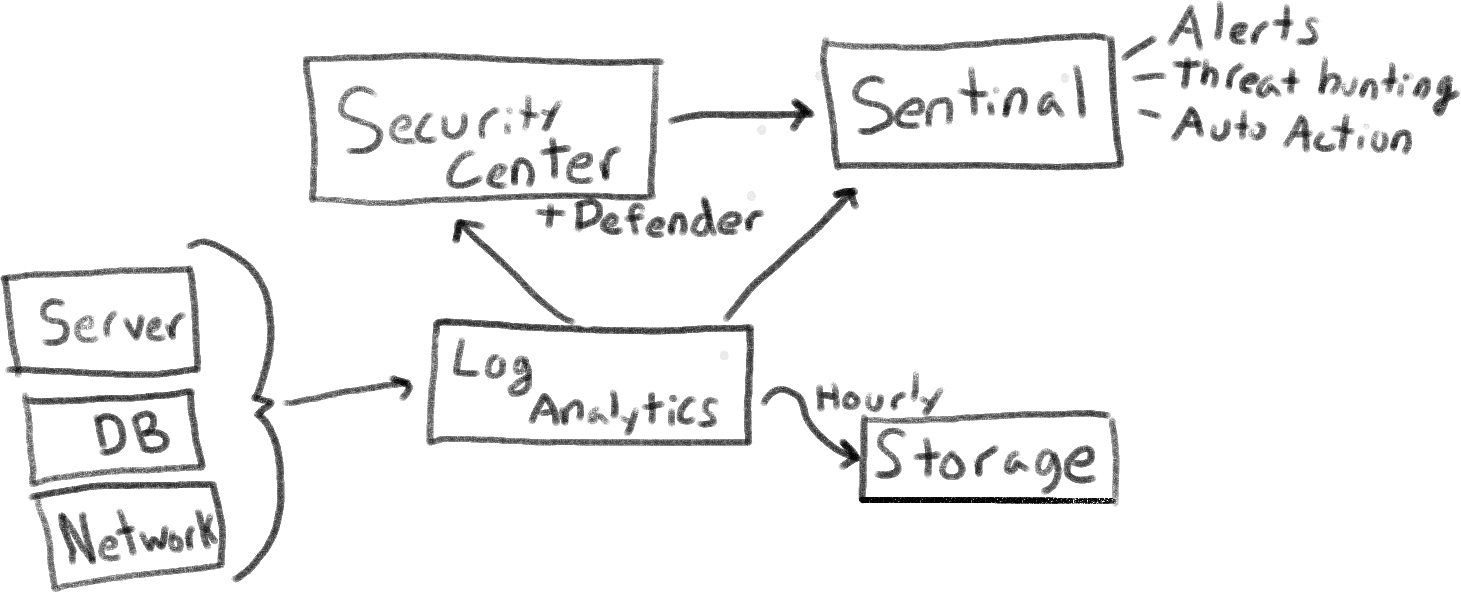
That's a lot! Thankfully, most of this is pretty easy to configure. Let's jump in!
Centralizing Logs with Log Analytics
Your operations team may already be collecting logs and alerting based on performance metrics. We just need to ensure that the logs we care about are also being ingested. In particular you may want to look at your AD logs, server syslogs, and any security product logs you have deployed.
To configure Log Analytics, log into the Azure Portal, and create a new Log Analytics Workspace. You could create a template here, but using the web interface is simple enough, since you are unlikely to create many of these resources. Allow Azure to deploy the instance, and once deployed, you can automatically connect assets to your analytics instance.
Log Analytics has a cost - both based on ingestion and total storage used. In addition, the maximum retention time for logs is 2 years, which may not be enough for all organizations. I recommend saving security sensitive logs as long as possible, in case they are needed in future investigations. There is a great write up (and playbook) on how to configure this by Microsoft.
Setup Security Center & Defender
With logs being aggregated, we are now ready to setup security center. You'll need a role with Security Admin access to setup and configure everything.
To fully utilize security center, you'll also need the Azure monitoring agent deployed to assets. Security Center will show you un-monitored assets, and deploying agents can be done from within the asset control panel in most cases.
Security Center is helpful for finding recommendations on general cloud security health - for instance coming up with general security improvements such as full disk encryption, or comparing your deployment against security standards.
Azure will also push the cost-plus Defender service pretty hard, and attempt to sell you an upgrade. I recommend you do the upgrade, at least on all internet facing assets and critical system components. It is required for advanced monitoring and for out of the box compliance and regulatory assessments. The cost is less than similar functionality from other security vendors in my experience.
The first thing we'll do is add some regulatory standards to our compliance dashboard. Even if you don't have to adhere to them currently, I find that they provide a solid baseline, and Microsoft provides several out of the box. To Enable one, click the compliance box from the dashboard, then manage compliance policies, and add ones to for each subscription.
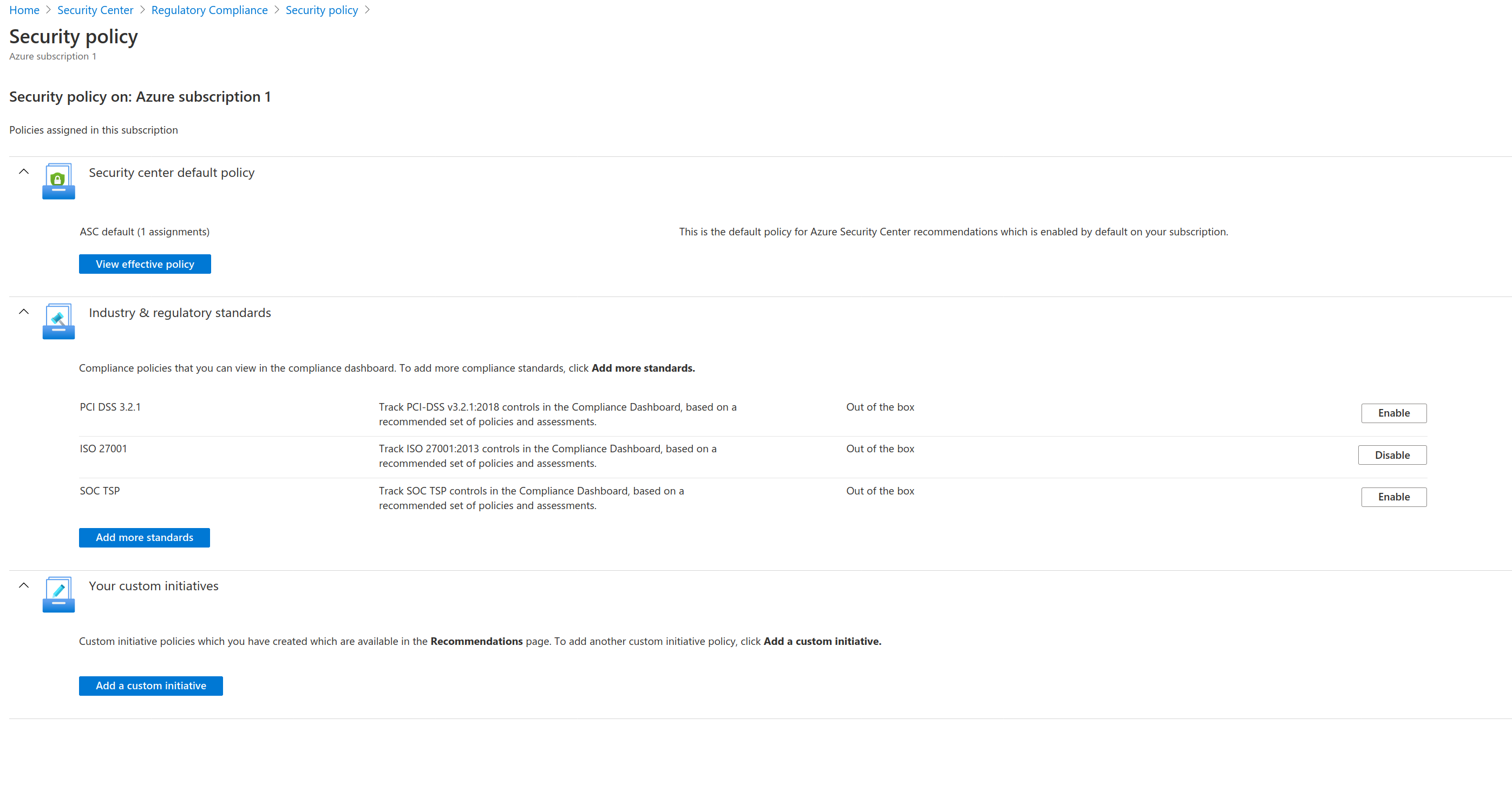
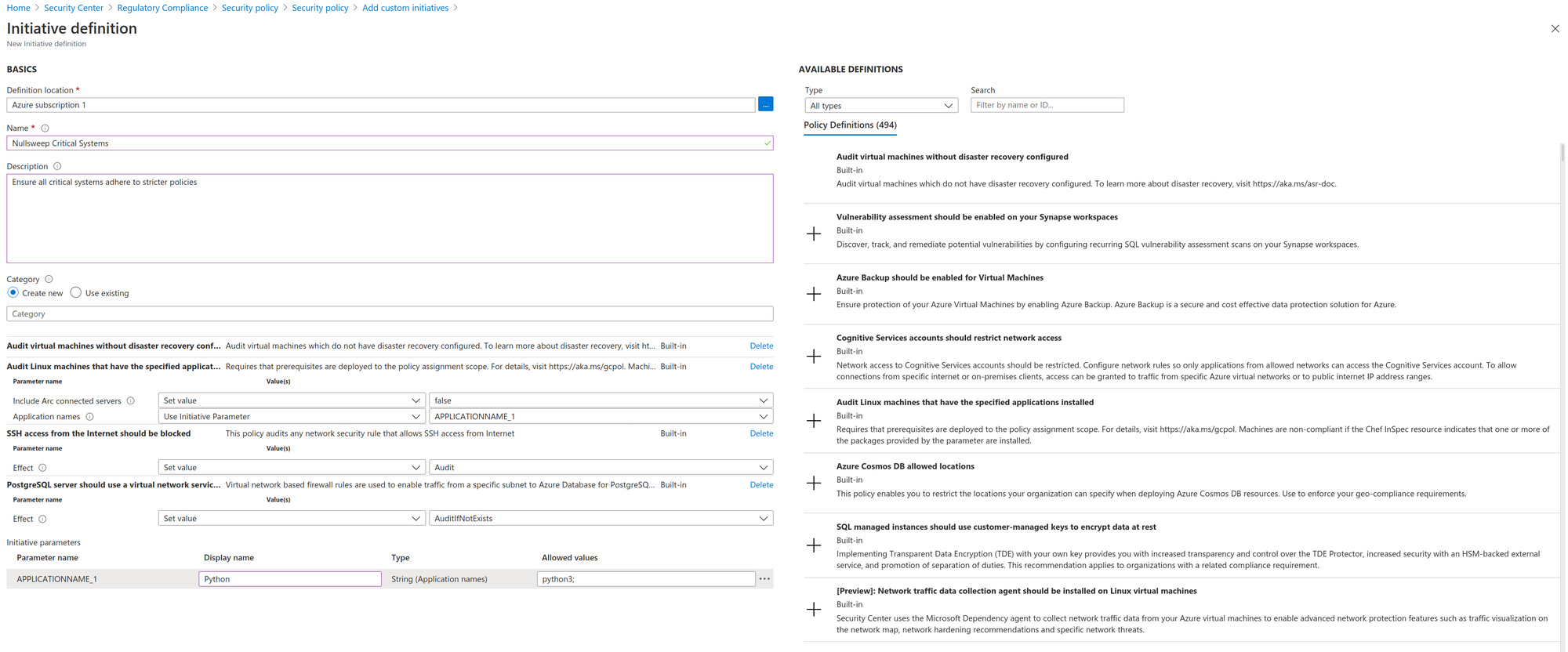
I also suggest you craft your own, stricter policy groups for auditing. Security Center has more than 500 rules you can quickly add to a custom compliance group - everything from network rules to specifying that all servers have a particular application installed (such as a security agent). Of course, you can also write your own policies specific to your organization, but how to do that is out of scope for this post.
In the below screenshot, I have created a policy group that ensures SSH is not accessible from the internet, my machines should have Disaster Recovery configured, Linux servers should have python installed (though in reality this would more likely be things like your HIDS agent or other security software), and that Postgres has some kind of network protection.
Setup Sentinel for your SIEM
You may already have a SIEM that is integrated with your processes.
Start by connecting the Log Analytics instance(s) setup in the first step of this article. I won't go through all the setup steps here, because the Azure documentation already has good tutorials. Here are some to get started:
- Setup built in workbooks
- Enable out of the box detection rules (You can also create custom rules if you have some proprietary or purchased rule sets)
- Setup automated responses and alerts
Finally, you may want to leverage these features in Sentinel, but continue to use a different SIEM (such as splunk) for triage. Sentinel can be integrated with other systems, but you'll have to check with your SIEM vendor or setup some kind of custom data export. For splunk, they offer an Azure connector.
Conclusions and other Resources
Implementing these services and spending some time thinking about how to leverage them in your organization will build a solid base for an Azure security program.
You'll have aggregated logs for security analysis, at a glance compliance - both regulatory and specific to your organization, and the ability to identify and respond to threats.
From here, you can write tailored custom policies to improve the overall security posture of the organization and automate responses to commonly seen threats.
Due to the breadth of the these services, I didn't go too in depth into any single service. Here are some excellent resources for learning more:
- John Savill's Azure Master Class - monitoring & security portion
- The same master class, Governance (policies)
- Azure security documentation (It's generally good, but can be hard to link all the various pieces you will need together)
- Azure security community (tons of good articles to find)


