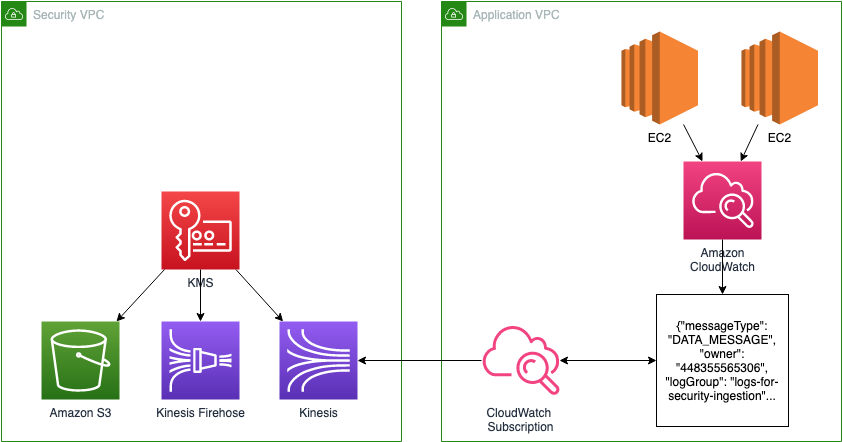
Centralized Security Logging in AWS
CloudFormation templates and walk-through to setup detailed security logging in multiple AWS accounts, centralized into a security account.
A Better Way to SSH in AWS (With RDS tunneling and security automation)
Setup and use System and Session Manager to replace bastion hosts for SSH and RDS tunnels. Automate security tasks on servers with automation documents.
Advanced AWS Security Architecture
A series of articles implementing advanced security controls on AWS, leveraging build in aws security tooling and security best practices.
Subdomain_recon.py: A SubDomain Reconnaissance Tool
A tool to search for subdomain and nameserver takeover risks across an organization, written in python.
Deploying Docker Securely
Common docker deployment pitfalls and how to mitigate them when deploying a container to infrastructure you control.
A Pivot Cheatsheet for Pentesters
Quick walkthrough of pivot techniques including ssh, meterpreter, ncat, and netcat.
A NoSQL Injection Primer (with Mongo)
An introduction to NoSQL and JavaScript Injections, with a sample vulnerable NodeJS/Mongo application.
HTTP Security Headers - A Complete Guide
A description of each security header, why it is important, and how to configure your website in a secure way.
Empathizing With Threat Actors
Empathy is a powerful tool in human relationships, but often it seems to be disregarded when talking about more technical realms such as security.